One of my goals before the end of the year is to protect my online accounts with multi-factor authentication. I’ve been protecting many of my identities with TOTP. TOTP is a great way to add multi-factor authentication to our identity. It adds the “something I have” to the “something I know”. However, I’m now running… Continue reading Authentication: Push
Tag: Gateway
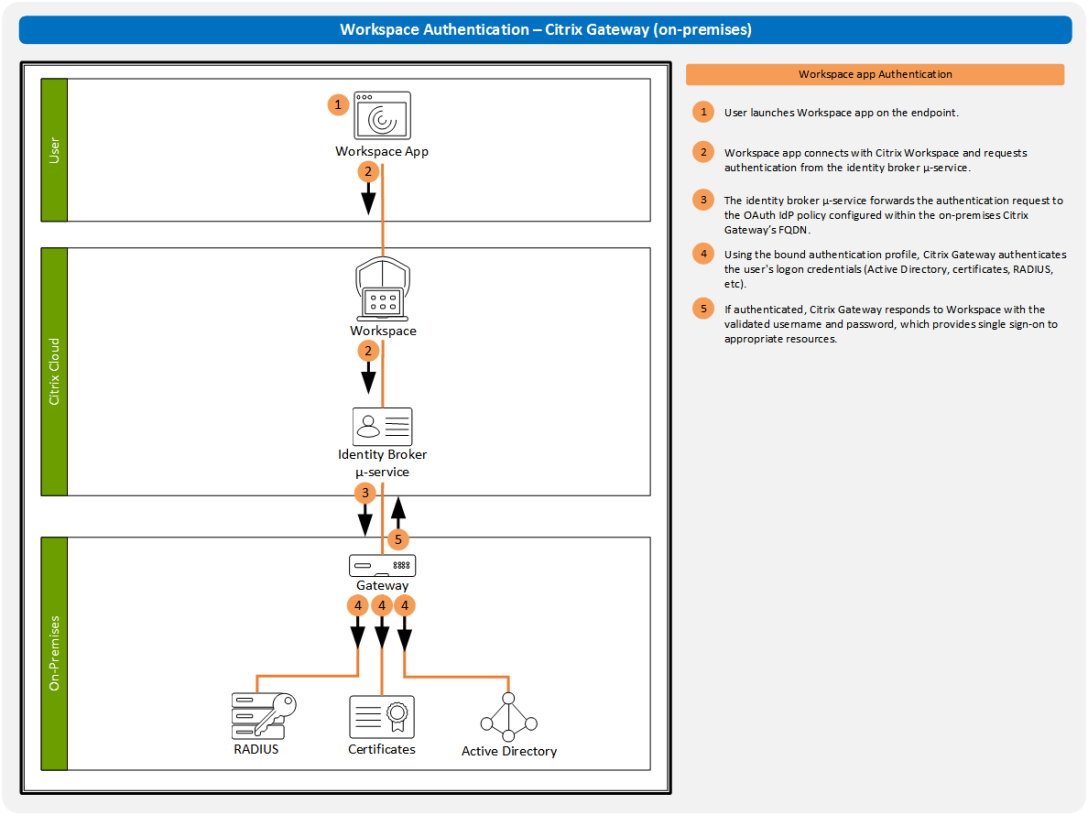
Citrix Workspace Authentication: Citrix Gateway
One of the challenges with using cloud services is getting the same experience you had in an on-premises deployment. For the past 20+ years, many Citrix Virtual Apps and Desktop deployments utilized a Citrix Gateway to provide an ICA proxy through the firewall. For external users, Gateway also authenticated those users. Over the years, admins… Continue reading Citrix Workspace Authentication: Citrix Gateway