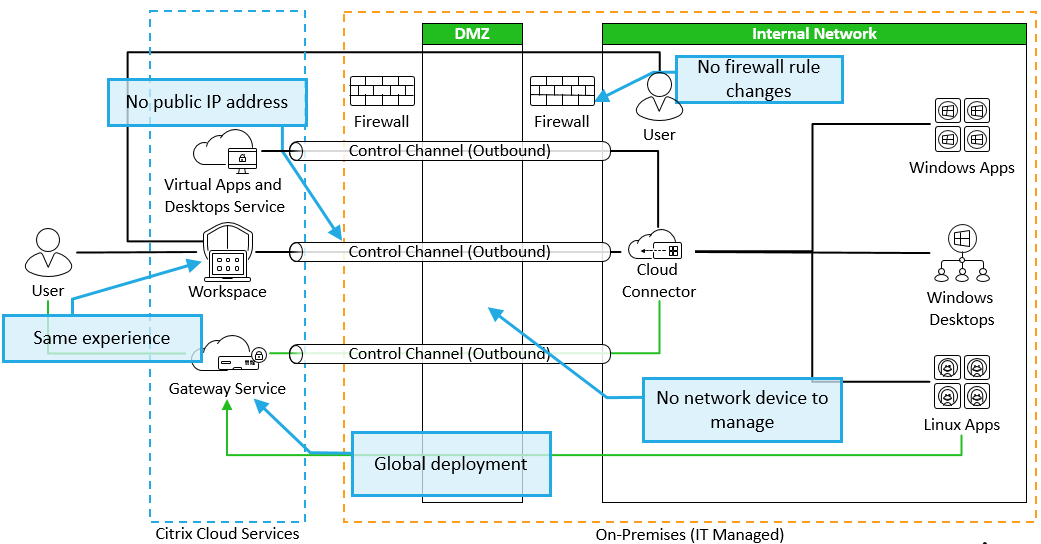
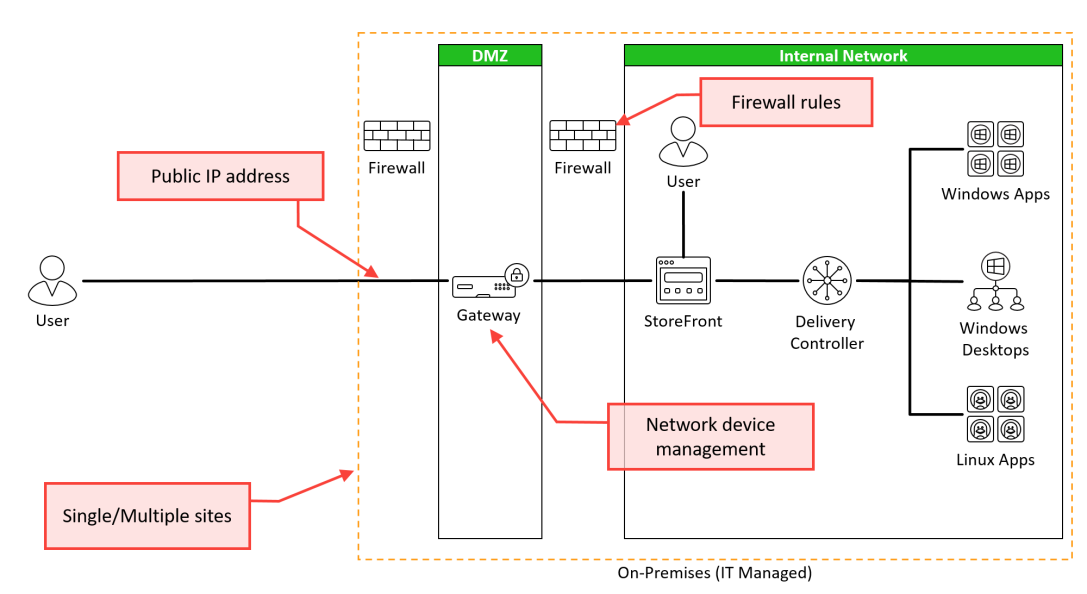
I don’t know of anyone who likes road construction, especially road construction that sends you on a multi-mile detour you around the construction. Detours are not as efficient as the direct route. They take more time for you to get to your destination. We will usually get the best experience if we can take the… Continue reading Direct Workload Connection
Tag: citrix
Considerations for Cloud Desktops – Skillset
Many moons ago when I first got my driver’s license, I remember driving down the road in the small town I grew up in. All of the sudden, the engine dies. Luckily, I was able to coast into a parking lot. I parked the car and popped the hood. I’m not sure what I expected… Continue reading Considerations for Cloud Desktops – Skillset
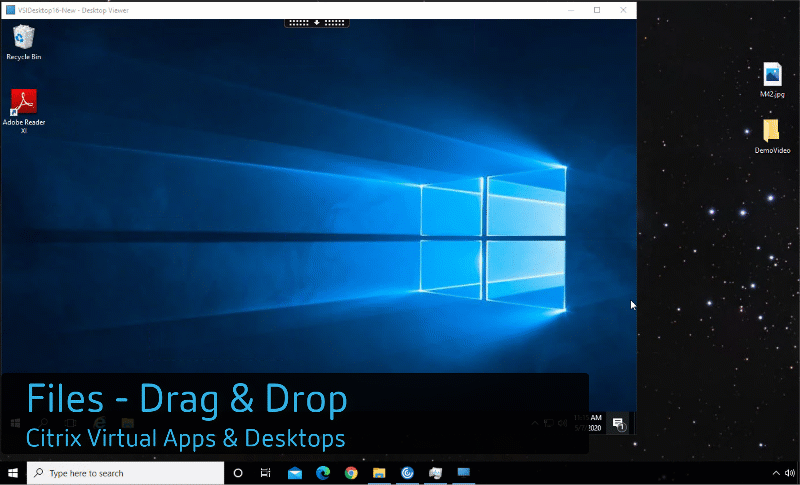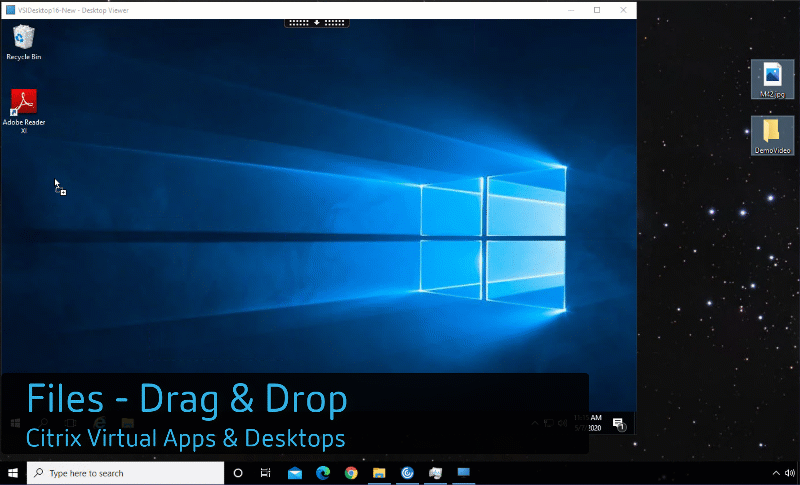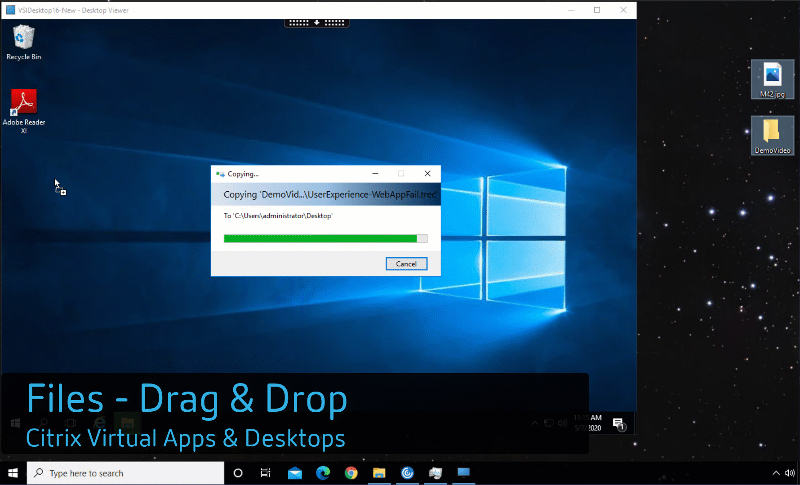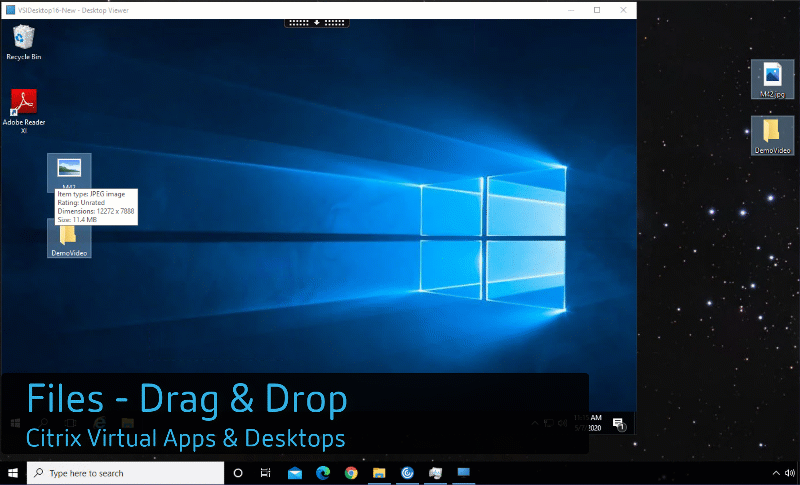
Drag and Drop
I typically spend most of my day working within my VDI environment. All of my apps and content are within the virtual desktop. However, from time-to-time, I have to do work on my end point device (typically it is because I’m capturing configuration images from within my home lab). Somehow I need to get the… Continue reading Drag and Drop
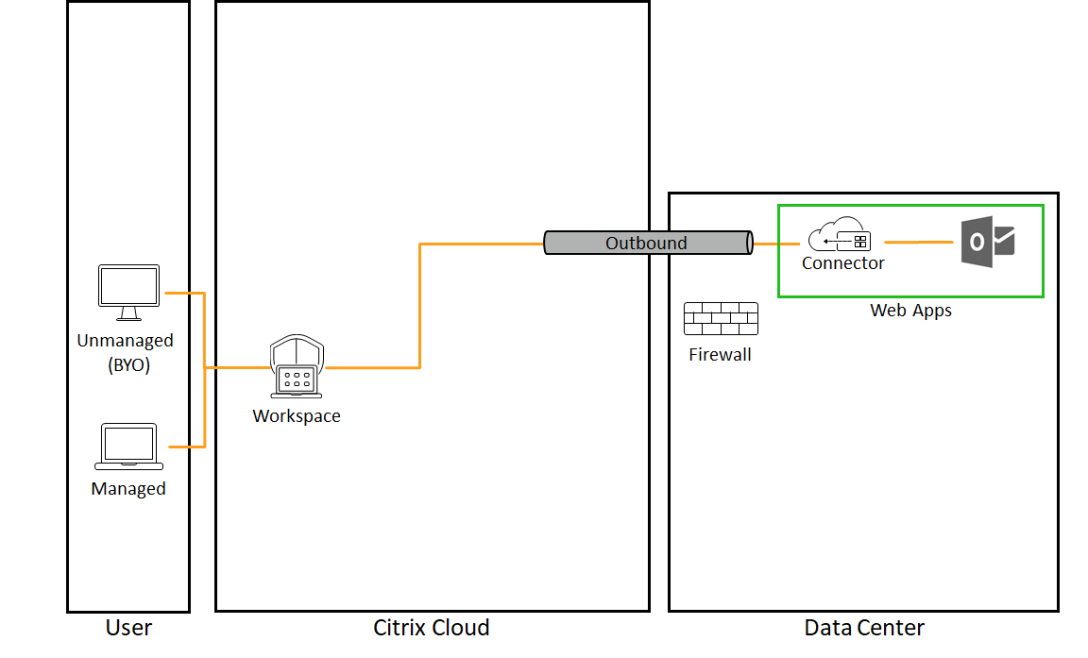
VPN Alternative for Web Apps
There are many technologies out there to continue letting let people work while stuck at home. A big part of the solution you use all comes down to what your typical day looked like. And by typical, I’m talking about life before lockdown. Where you an office-based user? What types of apps did you access?… Continue reading VPN Alternative for Web Apps
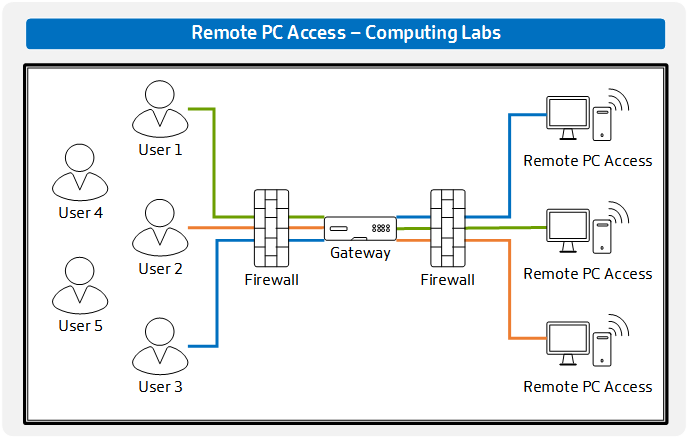
Remote PC Access – For Computing Labs
Using Remote PC Access for Office Workers is an extremely easy use case where we have a 1:1 relationship between users and PCS. But what about computing labs where the relationship changes from 1:Many? This type of architecture looks slightly different. A few things to be aware of with computing labs Computing labs typically have… Continue reading Remote PC Access – For Computing Labs
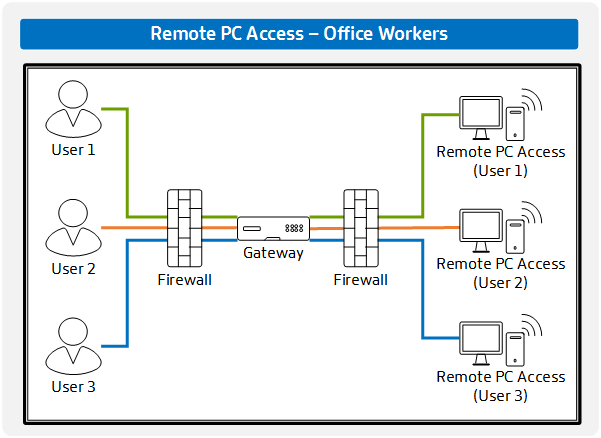
Remote PC Access – For Office Workers
Within Citrix Virtual Apps and Desktops, there has been a hidden gem called Remote PC Access. For many people who commute to work, they sit in the same chair in front of the same PC. In it’s simplest terms, Remote PC Access simple moves that chair away from the PC. This simplified architecture shows what… Continue reading Remote PC Access – For Office Workers
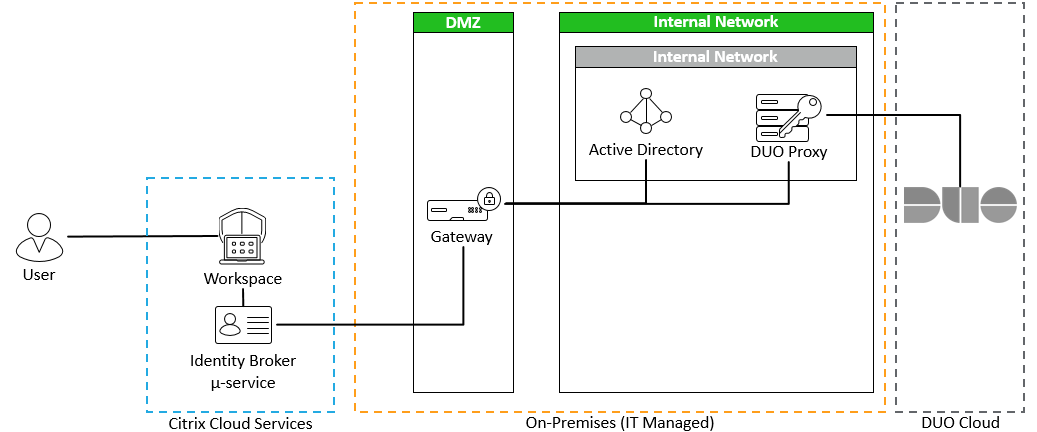
Citrix Workspace Authentication: Duo
A user’s primary identity authorizes access to the Workspace. A username and password is not a strong authentication policy. Passwords are problematic. We know we need to provide multi-factor authentication. And within Citrix Workspace, the options continue to expand. So far, I’ve been able to demonstrate how to integrate the following with Citrix Workspace: Active… Continue reading Citrix Workspace Authentication: Duo
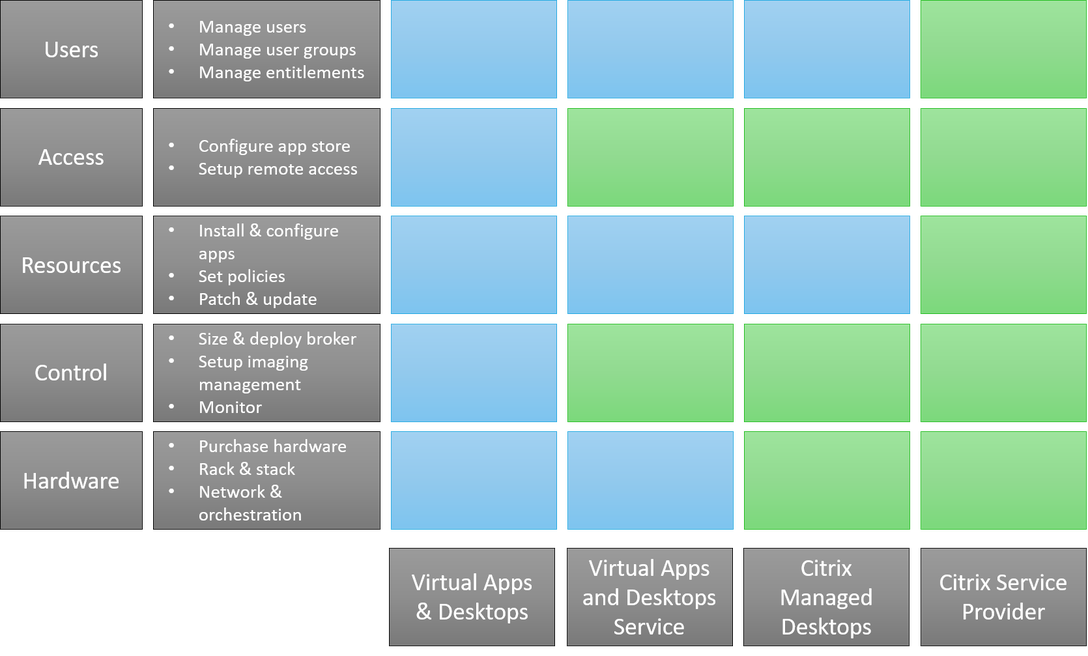
VDI Deployment Options
I enjoy having choices. I like having choices between Hefeweizen, Amber and Pale Ales. I like having a choice between playing Fallout, Mass Effect and Lego Star Wars. I like having a choice between mountain biking, tennis or hiking (yes, you can do all of these in the winter in Minnesota). I also have a… Continue reading VDI Deployment Options
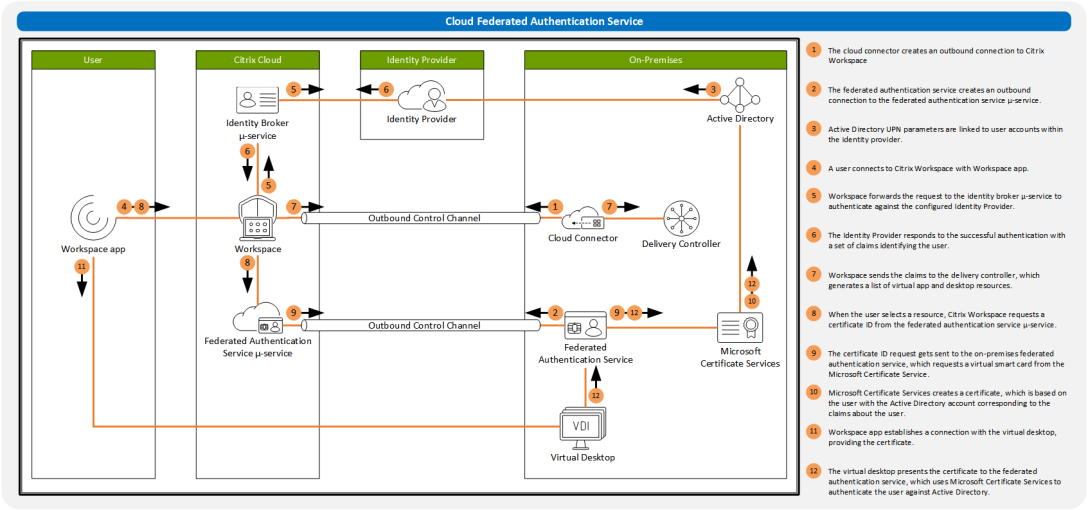
Citrix Workspace Authentication: Federated Authentication Services
I have one primary key to let me into my house. Once I’m inside my house, I can see many resources that I might want to use like a bed, bathroom, safe, TV and a freezer. However, some of these resources are secured with a different key. I might have a code to access NetFlix.… Continue reading Citrix Workspace Authentication: Federated Authentication Services
Authentication: Push
One of my goals before the end of the year is to protect my online accounts with multi-factor authentication. I’ve been protecting many of my identities with TOTP. TOTP is a great way to add multi-factor authentication to our identity. It adds the “something I have” to the “something I know”. However, I’m now running… Continue reading Authentication: Push