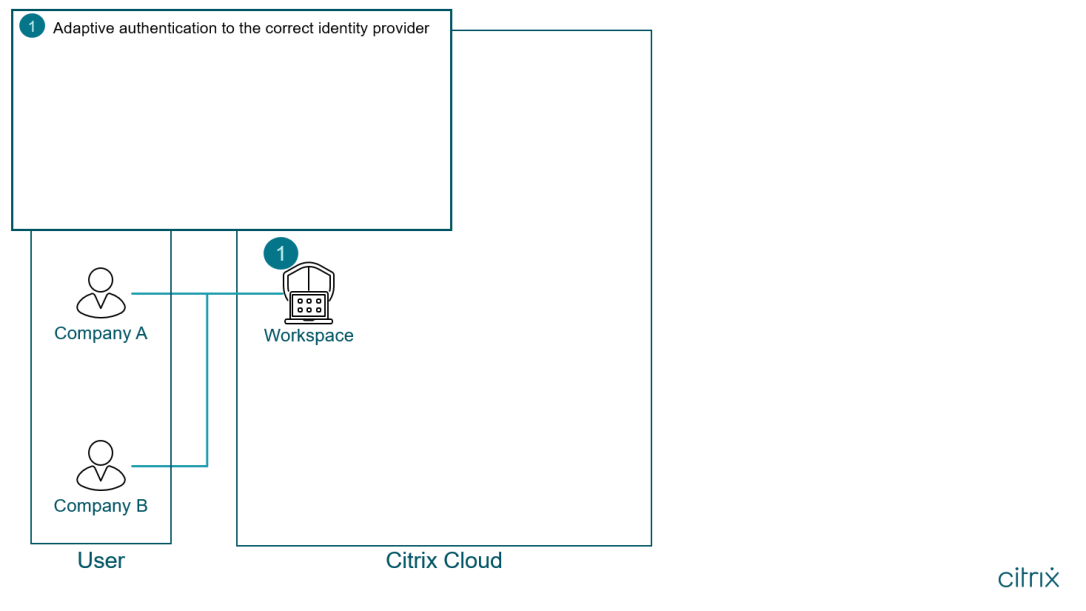
Those of us in IT understand the complexities with integrating two separate IT environments into one because of a merger/acquisition. How can we provide access to apps from another company with a zero trust network access (ZTNA) strategy? This was something recently detailed in the following items Reference Architecture: Zero Trust Mergers & Acquisitions StrategyUser… Continue reading Zero Trust M&A Strategy: Adaptive Authentication
Tag: okta
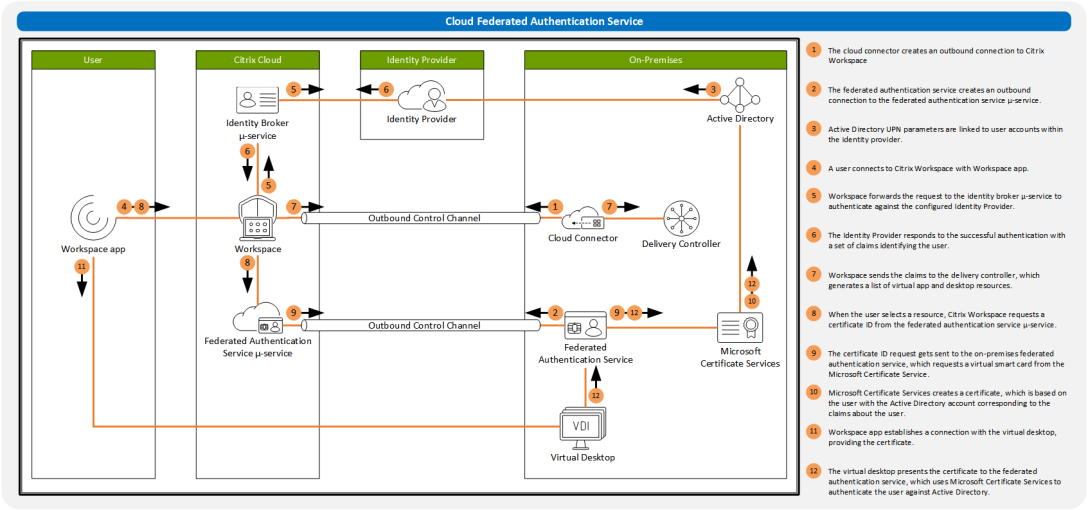
Citrix Workspace Authentication: Federated Authentication Services
I have one primary key to let me into my house. Once I’m inside my house, I can see many resources that I might want to use like a bed, bathroom, safe, TV and a freezer. However, some of these resources are secured with a different key. I might have a code to access NetFlix.… Continue reading Citrix Workspace Authentication: Federated Authentication Services
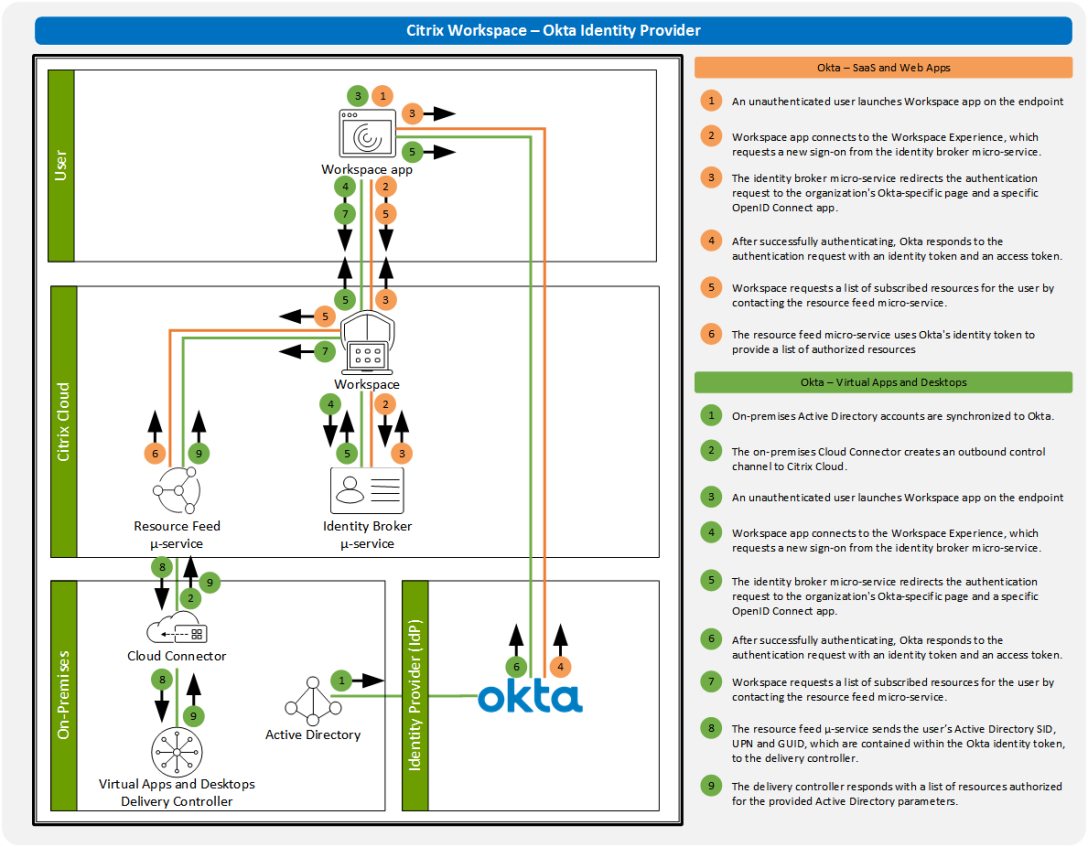
Citrix Workspace Authentication: Okta
None of us likes starting over. So if we don’t have to, why would we? Unfortunately, with technology, many of us are forced to to follow a single path. That single path often requires us to start over. But this is one of the interesting things about Citrix Workspace and the user’s primary identity… Don’t… Continue reading Citrix Workspace Authentication: Okta
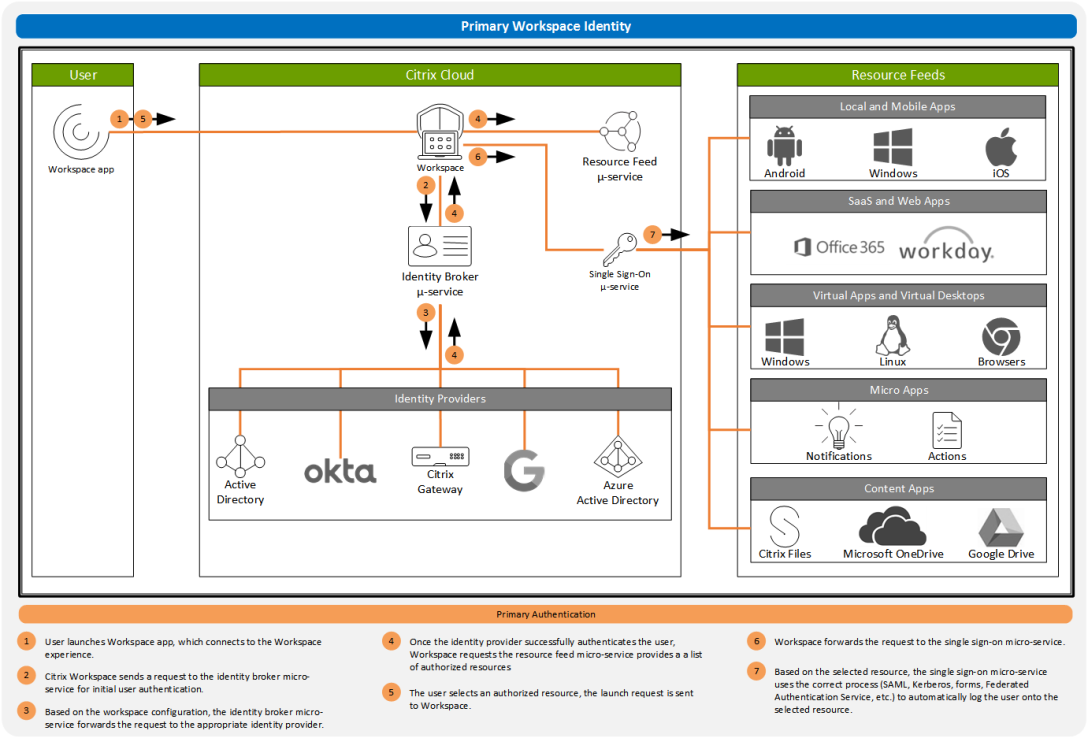
Citrix Workspace Authentication: Overview
One of the major issues with the current state of the end user computing environment is the number of identities a user is required to remember. Almost every service or application a user subscribes to requires the user create a new identity and password. With so many identities, almost all of us use the same… Continue reading Citrix Workspace Authentication: Overview