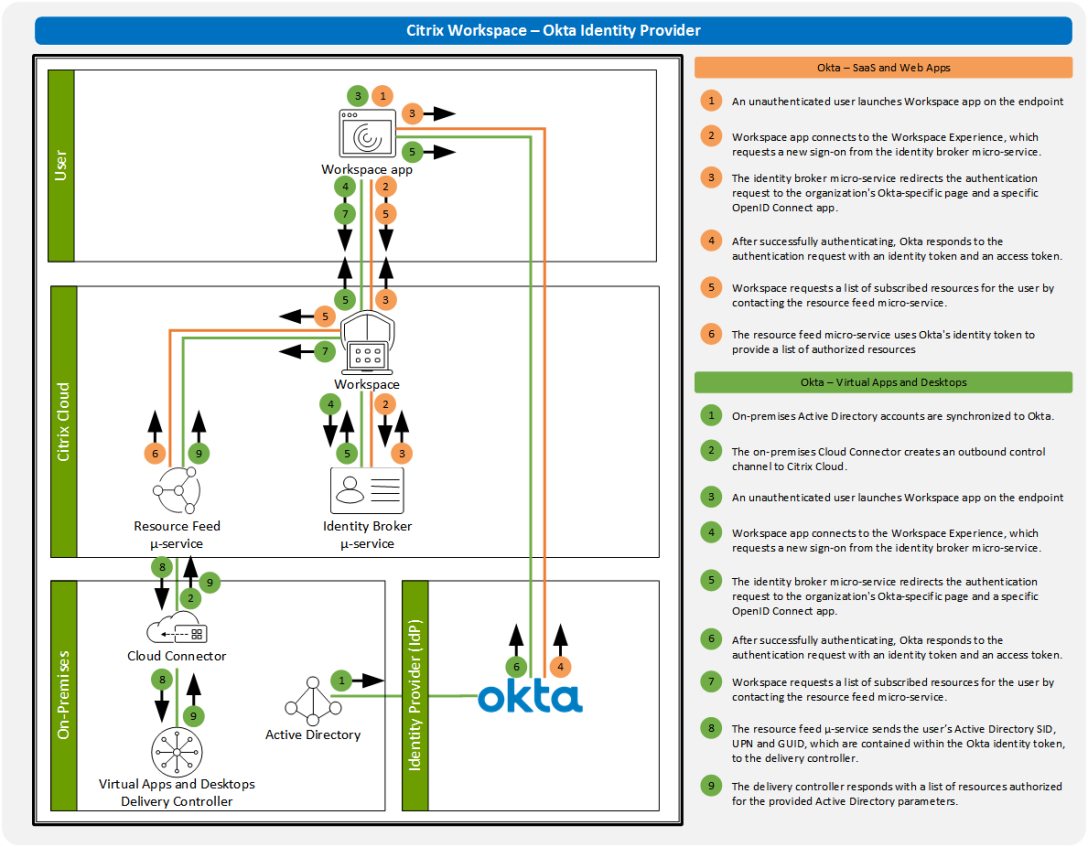
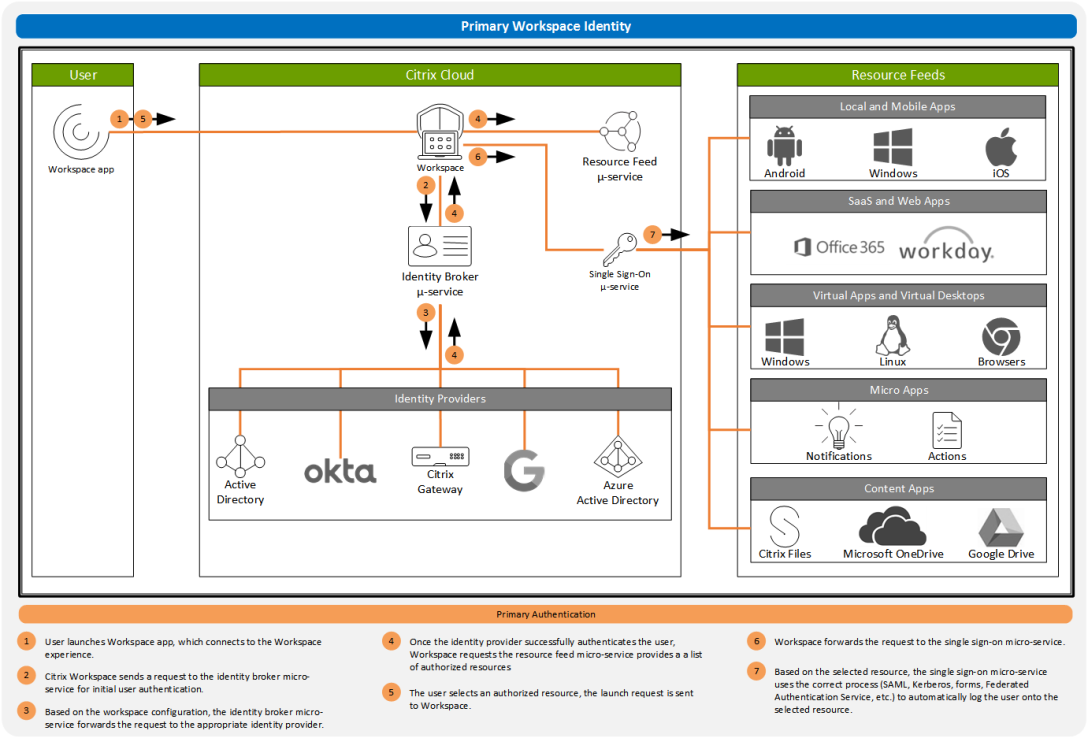
None of us likes starting over. So if we don’t have to, why would we? Unfortunately, with technology, many of us are forced to to follow a single path. That single path often requires us to start over. But this is one of the interesting things about Citrix Workspace and the user’s primary identity… Don’t… Continue reading Citrix Workspace Authentication: Okta
Tag: MFA
Citrix Workspace Authentication: Overview
One of the major issues with the current state of the end user computing environment is the number of identities a user is required to remember. Almost every service or application a user subscribes to requires the user create a new identity and password. With so many identities, almost all of us use the same… Continue reading Citrix Workspace Authentication: Overview
Authentication: TOTP
Let’s make one thing perfectly clear… TOTP ≠ OTP OTP = One-Time Password TOTP = Time-based One-Time Password As discussed in the Two-Step Verification post, OTP sends the one-time password to the user’s mobile phone via SMS or to the user’s email address. TOTP, on the other hand, uses a local app on the mobile… Continue reading Authentication: TOTP
Authentication: Two-Step Verification
So far, I’ve realized the following I have way too many identities Password complexity rules are implemented incorrectly Multi-factor authentication will provide additional authentication security So let’s look at one of the most basic forms of MFA. Unfortunately, I’ve seen this take on many names: Two-Step Verification Two-Step Authentication One-Time Password After providing your username… Continue reading Authentication: Two-Step Verification
Authentication: Passwords
<Sarcasm> Passwords. I love them. I love them so much, I have over 150 of them. </Sarcasm> We have our identity and we provide it to a system. In order to prove we are who we say we are, we need to authenticate. Passwords are one method for authentication. In theory, passwords are easy, but in… Continue reading Authentication: Passwords
Authentication: Your Identity
Most of us ignore authentication because it is seamless with us using our Active Directory username to log onto a domain-joined Windows 10 PC. But when we expand beyond Windows, there are so many other things to consider. I avoided learning about authentication for a long time. So many technologies. So many acronyms. So many… Continue reading Authentication: Your Identity