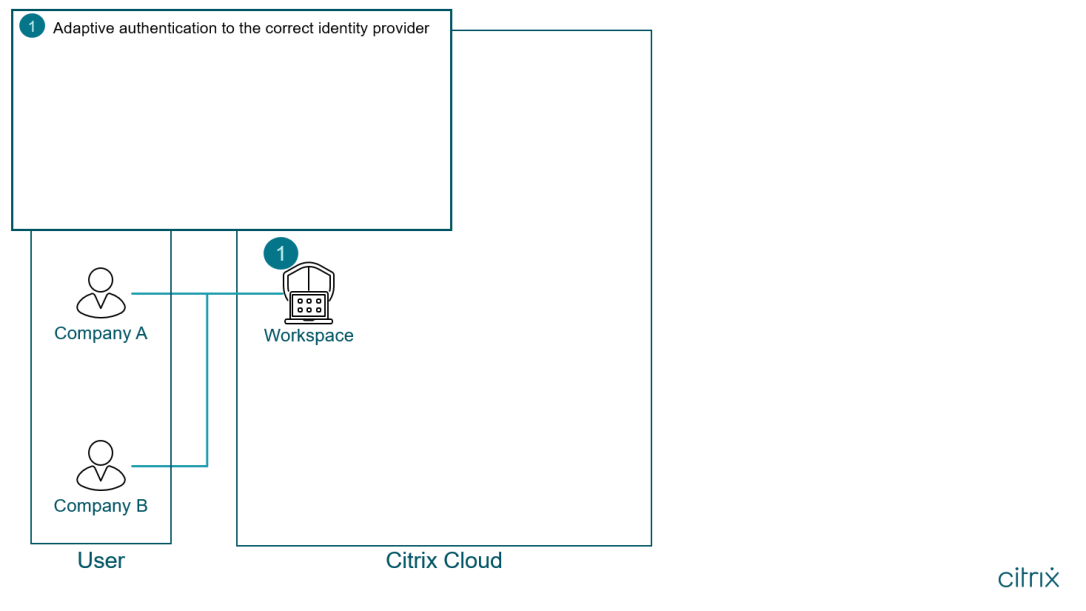
Those of us in IT understand the complexities with integrating two separate IT environments into one because of a merger/acquisition. How can we provide access to apps from another company with a zero trust network access (ZTNA) strategy? This was something recently detailed in the following items Reference Architecture: Zero Trust Mergers & Acquisitions StrategyUser… Continue reading Zero Trust M&A Strategy: Adaptive Authentication