For many of us, we’ve now experienced a few weeks of working from home. How’s it going? How’s your hygiene? Are you still bathing frequently? Have you found your rhythm? Now that you’ve had your first experiences with work from home, I wanted to provide some advice on how to make it the greatest thing… Continue reading Top 10 Practical Tips when Working From Home
Category: Uncategorized
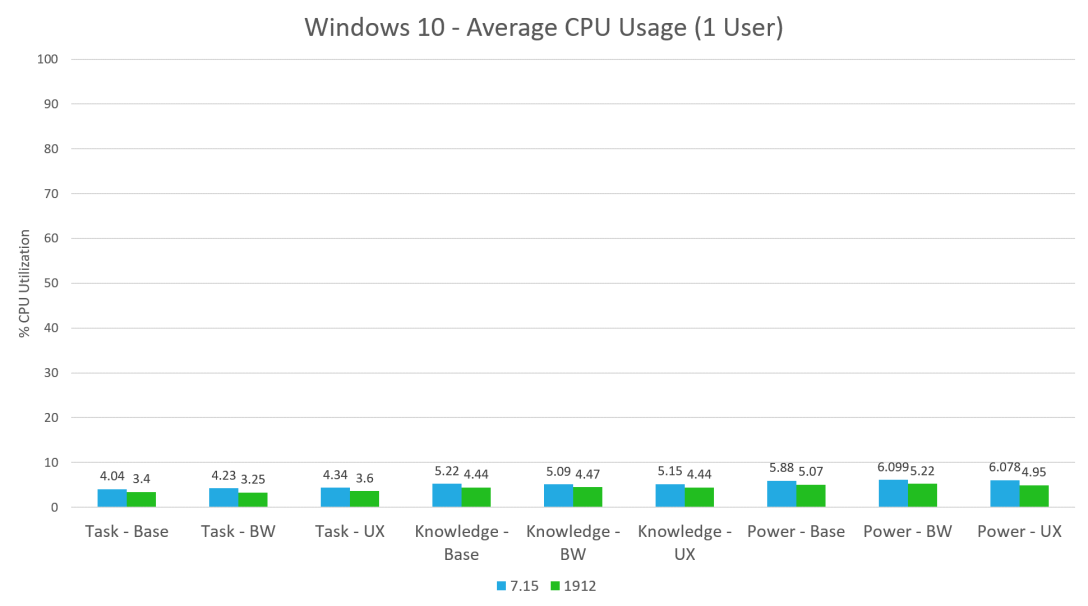
Citrix Virtual Apps and Desktops – CPU Utilization
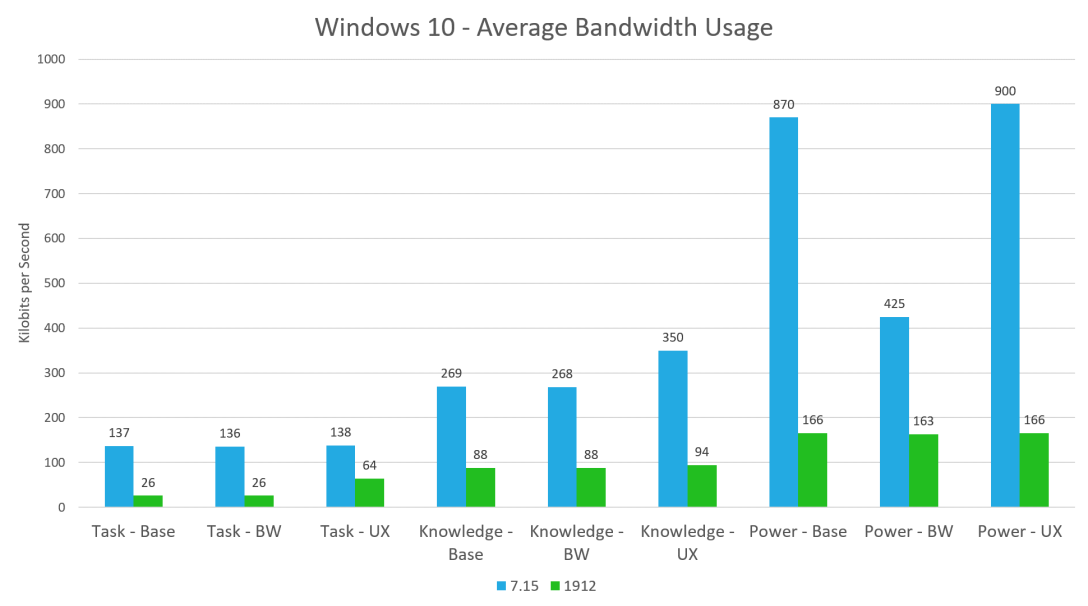
With the 1912 release of Citrix Virtual Apps and Desktops 1912, we saw a major improvement in overall bandwidth utilization. Some of the tests showed an 80% reduction in bandwidth utilization. But how does this drastic decrease in bandwidth utilization impact CPU utilization? Let’s find out. Test Details The test scenarios are as follows: Workloads:… Continue reading Citrix Virtual Apps and Desktops – CPU Utilization
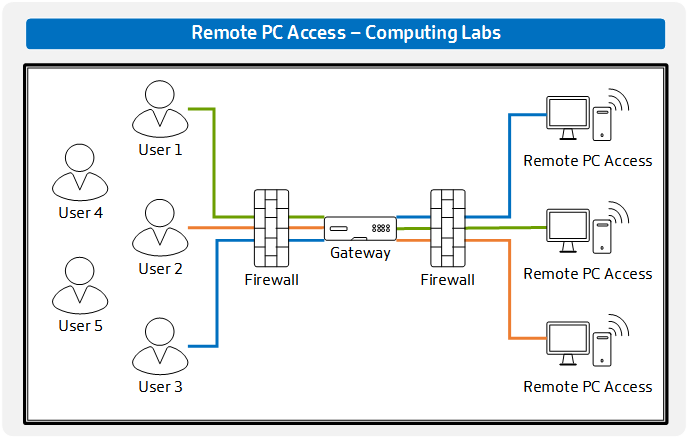
Remote PC Access – For Computing Labs
Using Remote PC Access for Office Workers is an extremely easy use case where we have a 1:1 relationship between users and PCS. But what about computing labs where the relationship changes from 1:Many? This type of architecture looks slightly different. A few things to be aware of with computing labs Computing labs typically have… Continue reading Remote PC Access – For Computing Labs
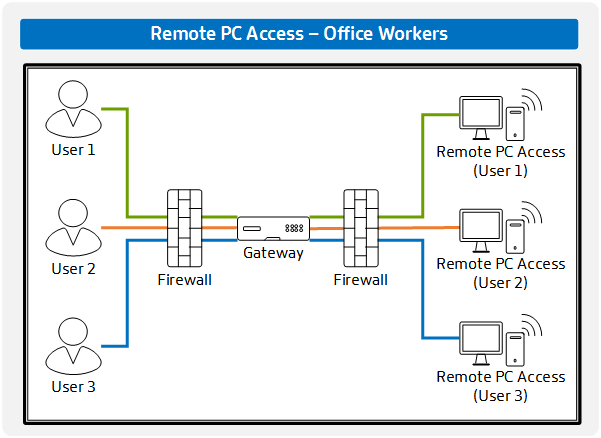
Remote PC Access – For Office Workers
Within Citrix Virtual Apps and Desktops, there has been a hidden gem called Remote PC Access. For many people who commute to work, they sit in the same chair in front of the same PC. In it’s simplest terms, Remote PC Access simple moves that chair away from the PC. This simplified architecture shows what… Continue reading Remote PC Access – For Office Workers
Citrix Virtual Apps and Desktops Bandwidth
With Citrix Virtual Apps and Desktops 1912 achieved LTSR (Long Term Servicing Release). This is the first LTSR since the 7.15 release, which was almost 3 years earlier. In 3 years, a lot has changed. The protocol had many improvements that directly impacted the user experience and bandwidth utilization. With each release, since 7.11 (2016),… Continue reading Citrix Virtual Apps and Desktops Bandwidth
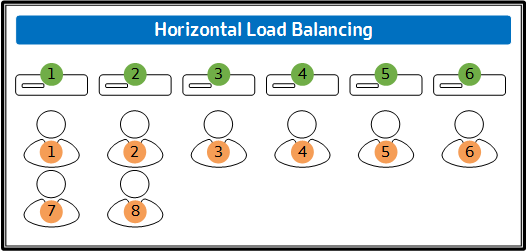
Vertical or Horizontal Load Balancing
Three years ago, I wrote the following best practices: Virtual Apps and Desktops Best Practice #4: To manage costs, focus on the right user experience instead of the best user experience. Typically, the better something is, the more it will cost. So you need to find that happy place where you align user experience with… Continue reading Vertical or Horizontal Load Balancing
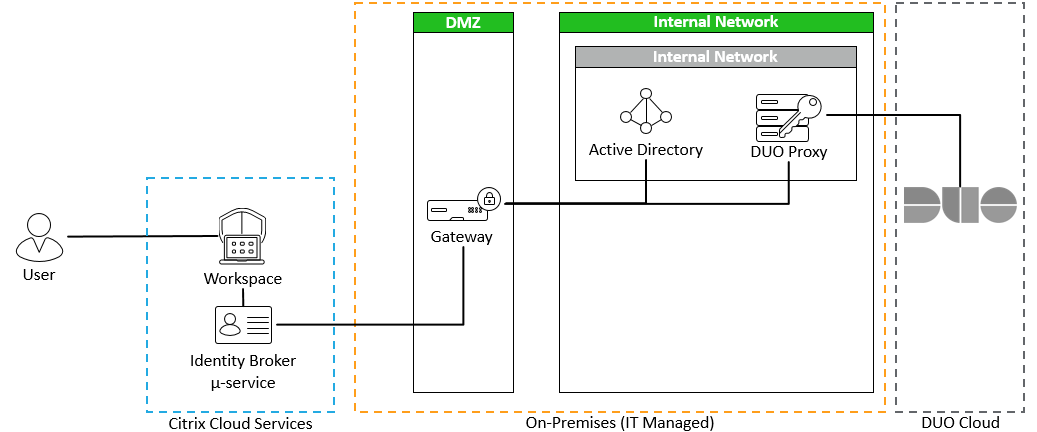
Citrix Workspace Authentication: Duo
A user’s primary identity authorizes access to the Workspace. A username and password is not a strong authentication policy. Passwords are problematic. We know we need to provide multi-factor authentication. And within Citrix Workspace, the options continue to expand. So far, I’ve been able to demonstrate how to integrate the following with Citrix Workspace: Active… Continue reading Citrix Workspace Authentication: Duo
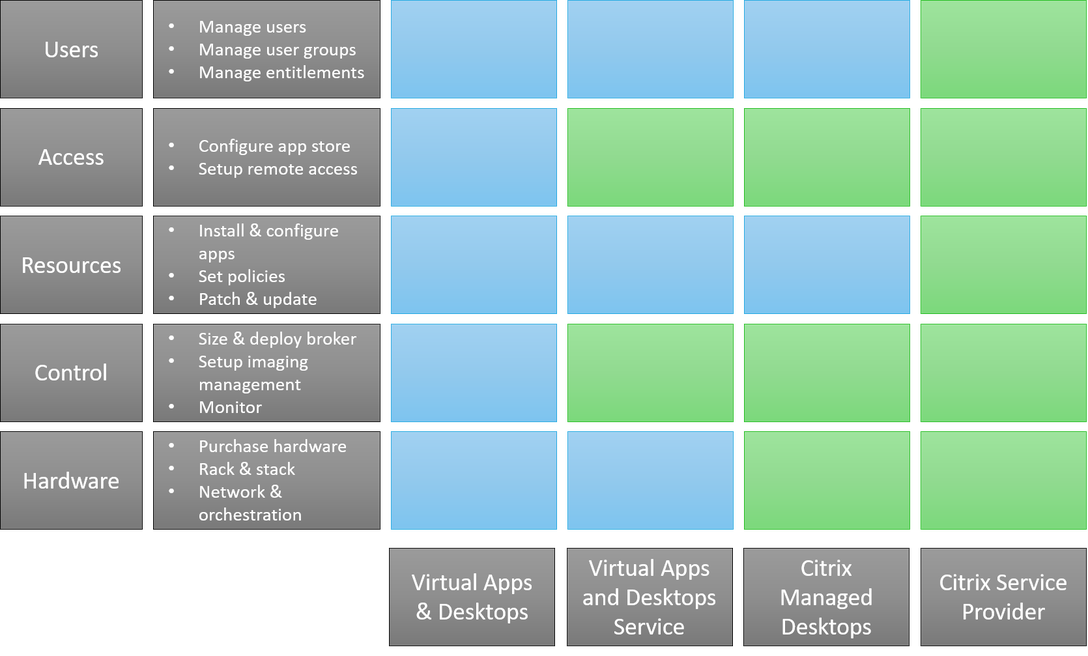
VDI Deployment Options
I enjoy having choices. I like having choices between Hefeweizen, Amber and Pale Ales. I like having a choice between playing Fallout, Mass Effect and Lego Star Wars. I like having a choice between mountain biking, tennis or hiking (yes, you can do all of these in the winter in Minnesota). I also have a… Continue reading VDI Deployment Options
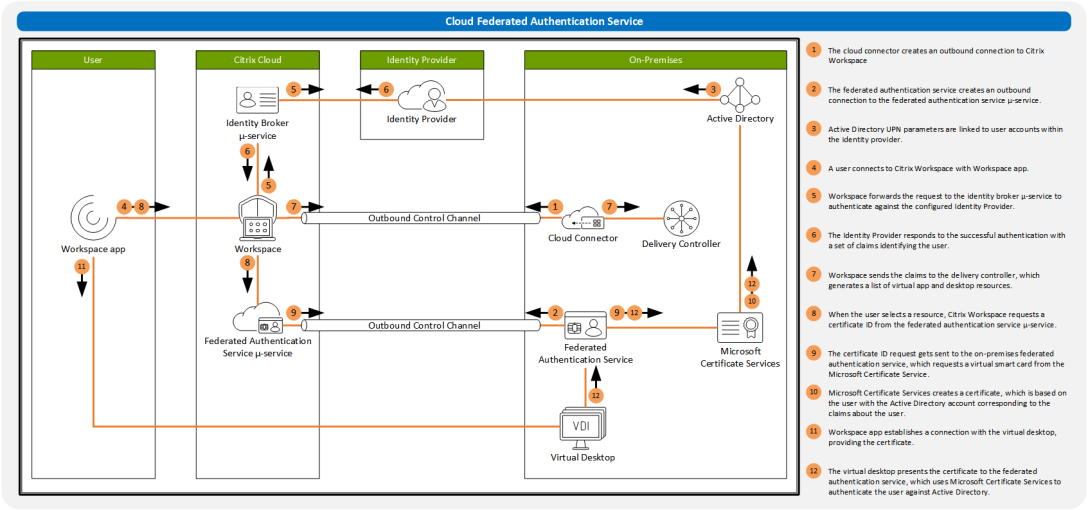
Citrix Workspace Authentication: Federated Authentication Services
I have one primary key to let me into my house. Once I’m inside my house, I can see many resources that I might want to use like a bed, bathroom, safe, TV and a freezer. However, some of these resources are secured with a different key. I might have a code to access NetFlix.… Continue reading Citrix Workspace Authentication: Federated Authentication Services
Authentication: Push
One of my goals before the end of the year is to protect my online accounts with multi-factor authentication. I’ve been protecting many of my identities with TOTP. TOTP is a great way to add multi-factor authentication to our identity. It adds the “something I have” to the “something I know”. However, I’m now running… Continue reading Authentication: Push