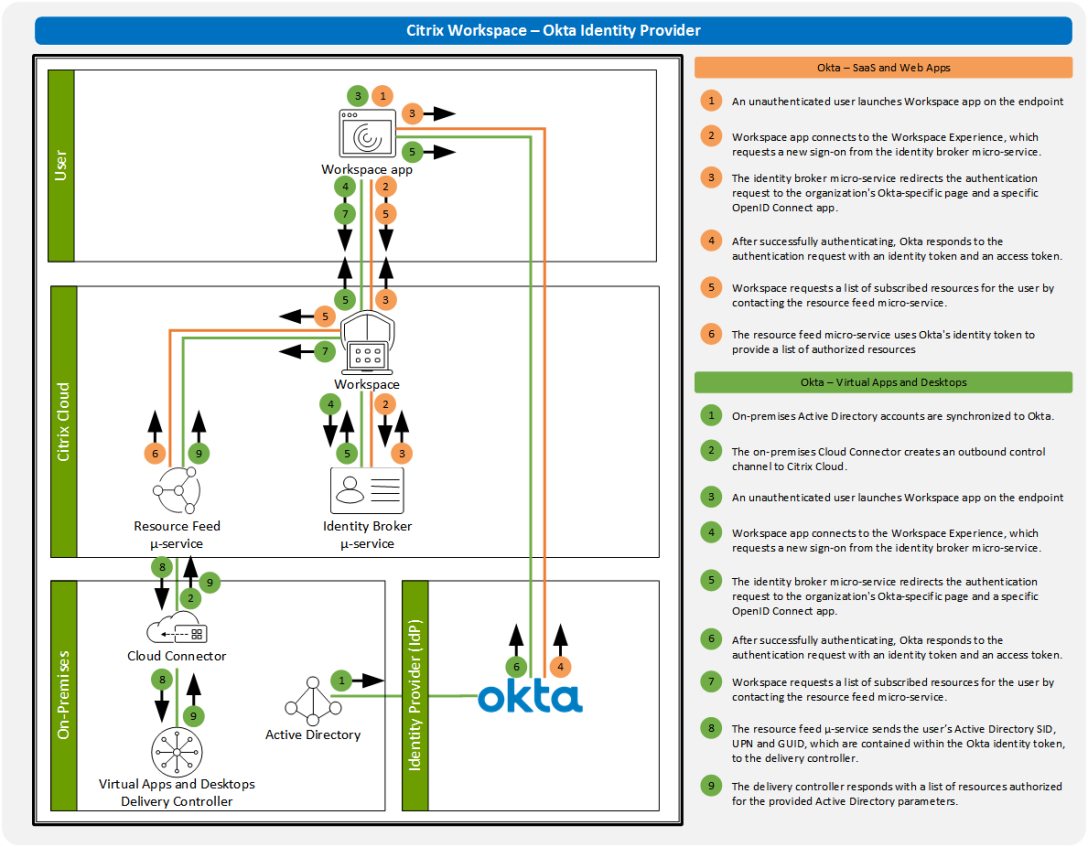
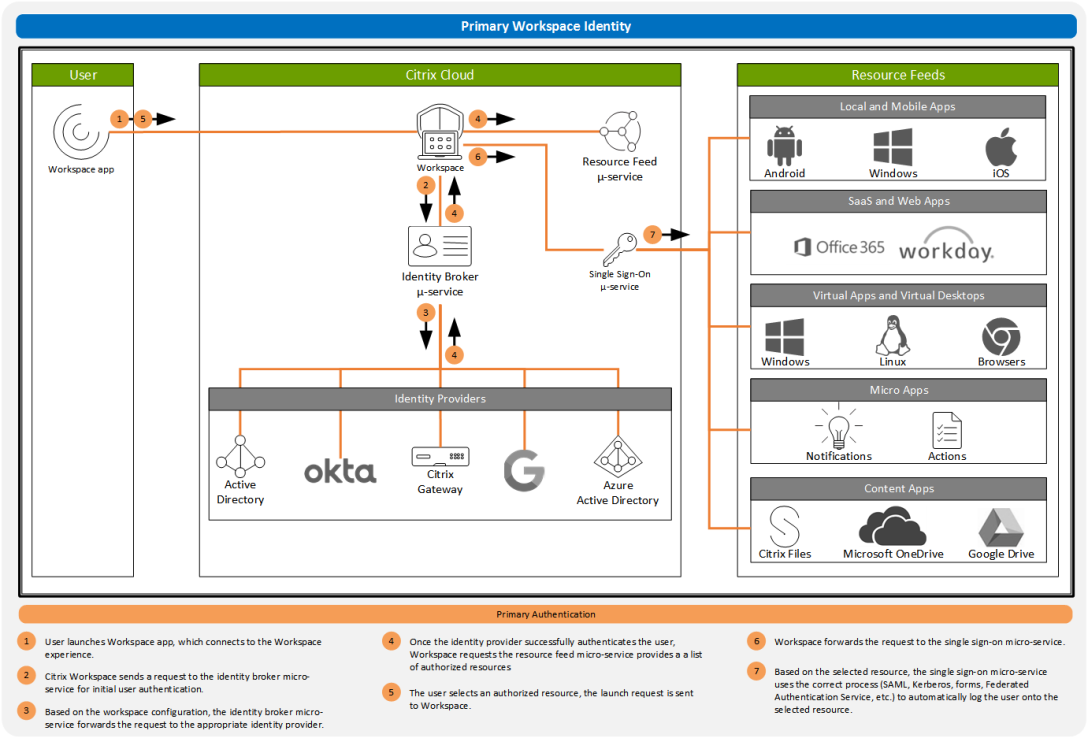
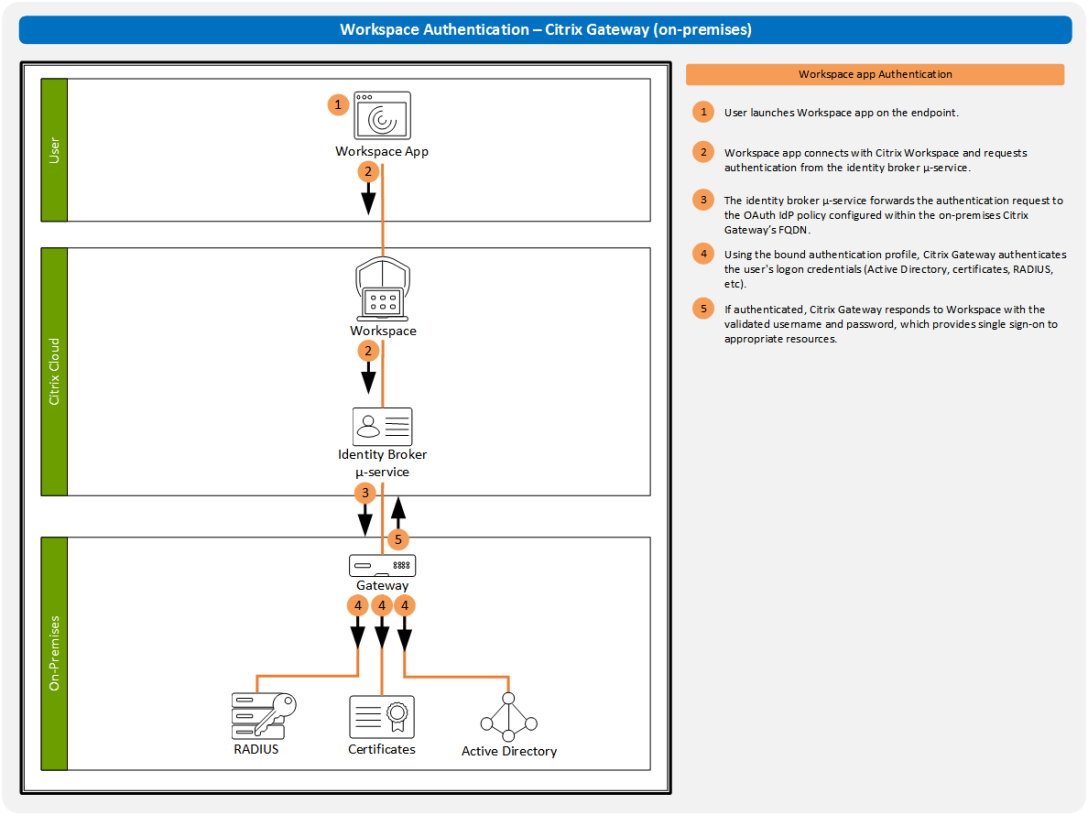
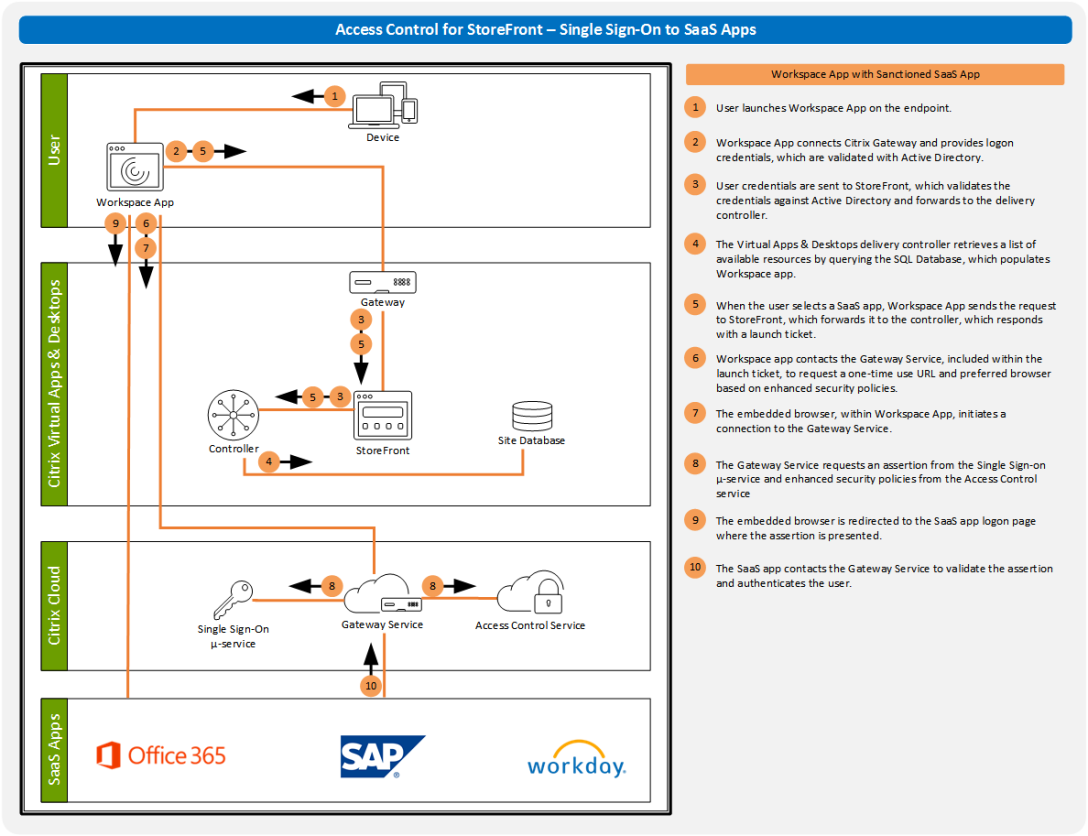
None of us likes starting over. So if we don’t have to, why would we? Unfortunately, with technology, many of us are forced to to follow a single path. That single path often requires us to start over. But this is one of the interesting things about Citrix Workspace and the user’s primary identity… Don’t… Continue reading Citrix Workspace Authentication: Okta
Category: Uncategorized
Citrix Workspace Authentication: Overview
One of the major issues with the current state of the end user computing environment is the number of identities a user is required to remember. Almost every service or application a user subscribes to requires the user create a new identity and password. With so many identities, almost all of us use the same… Continue reading Citrix Workspace Authentication: Overview
Citrix Workspace Authentication: Citrix Gateway
One of the challenges with using cloud services is getting the same experience you had in an on-premises deployment. For the past 20+ years, many Citrix Virtual Apps and Desktop deployments utilized a Citrix Gateway to provide an ICA proxy through the firewall. For external users, Gateway also authenticated those users. Over the years, admins… Continue reading Citrix Workspace Authentication: Citrix Gateway
Authentication: TOTP
Let’s make one thing perfectly clear… TOTP ≠ OTP OTP = One-Time Password TOTP = Time-based One-Time Password As discussed in the Two-Step Verification post, OTP sends the one-time password to the user’s mobile phone via SMS or to the user’s email address. TOTP, on the other hand, uses a local app on the mobile… Continue reading Authentication: TOTP
Access Control for StoreFront – Demo
I recently talked about how you can add SaaS and web applications to an on-premises StoreFront deployment. The integration goes beyond simply publishing links to the SaaS and web apps. The integration utilizes the Citrix Access Control service, providing SSO to SaaS No more passwords. No more access after employees have left the company. Enhanced… Continue reading Access Control for StoreFront – Demo
SaaS and Web Apps in StoreFront
In a Citrix Virtual Apps and Desktops deployment, many organizations use StoreFront to provide access to Windows and Linux applications and desktops. A lesser know feature, published content, can let StoreFront publish links to SaaS and web applications in an attempt to bring all resources together into a single view. (I see the differences between… Continue reading SaaS and Web Apps in StoreFront
Authentication: PIN
1, 2, 3, 4, 5 That’s the kind of thing an idiot would have on his luggage Let’s take a look at PIN-based authentication. Isn’t a PIN just like a password? Yes: A PIN is like a password in that a PIN is something you know No: A PIN is not like a password in… Continue reading Authentication: PIN
Authentication: Two-Step Verification
So far, I’ve realized the following I have way too many identities Password complexity rules are implemented incorrectly Multi-factor authentication will provide additional authentication security So let’s look at one of the most basic forms of MFA. Unfortunately, I’ve seen this take on many names: Two-Step Verification Two-Step Authentication One-Time Password After providing your username… Continue reading Authentication: Two-Step Verification
Updated IO Optimization with Machine Creation Services
With the Citrix Virtual Apps and Desktop 1903 release, Machine Creation Services continues to improve! The RAM-based write cache feature has been updated and improved. I wanted to see how the new RAM-based write cache capability compared to the previous version and how it compares to a desktop without using a RAM-based write cache. First,… Continue reading Updated IO Optimization with Machine Creation Services
Authentication: Passwords
<Sarcasm> Passwords. I love them. I love them so much, I have over 150 of them. </Sarcasm> We have our identity and we provide it to a system. In order to prove we are who we say we are, we need to authenticate. Passwords are one method for authentication. In theory, passwords are easy, but in… Continue reading Authentication: Passwords