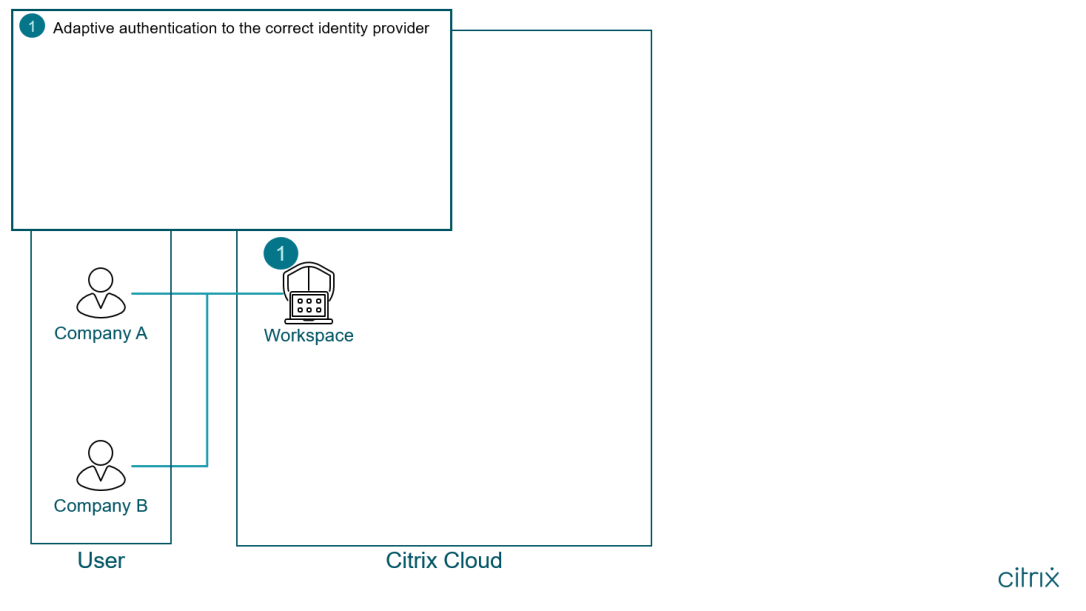
Those of us in IT understand the complexities with integrating two separate IT environments into one because of a merger/acquisition. How can we provide access to apps from another company with a zero trust network access (ZTNA) strategy? This was something recently detailed in the following items Reference Architecture: Zero Trust Mergers & Acquisitions StrategyUser… Continue reading Zero Trust M&A Strategy: Adaptive Authentication
Tag: Authentication
Authentication: Push
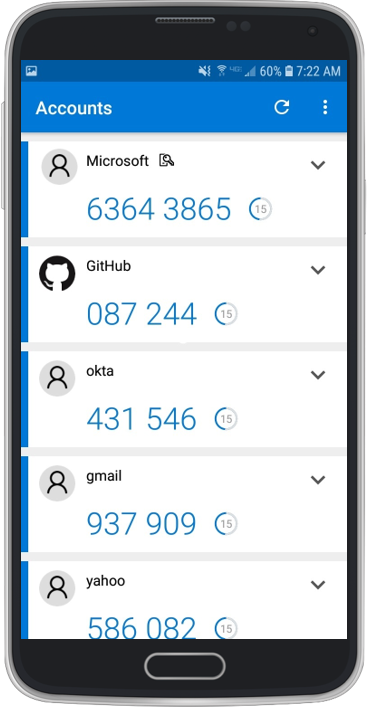
One of my goals before the end of the year is to protect my online accounts with multi-factor authentication. I’ve been protecting many of my identities with TOTP. TOTP is a great way to add multi-factor authentication to our identity. It adds the “something I have” to the “something I know”. However, I’m now running… Continue reading Authentication: Push
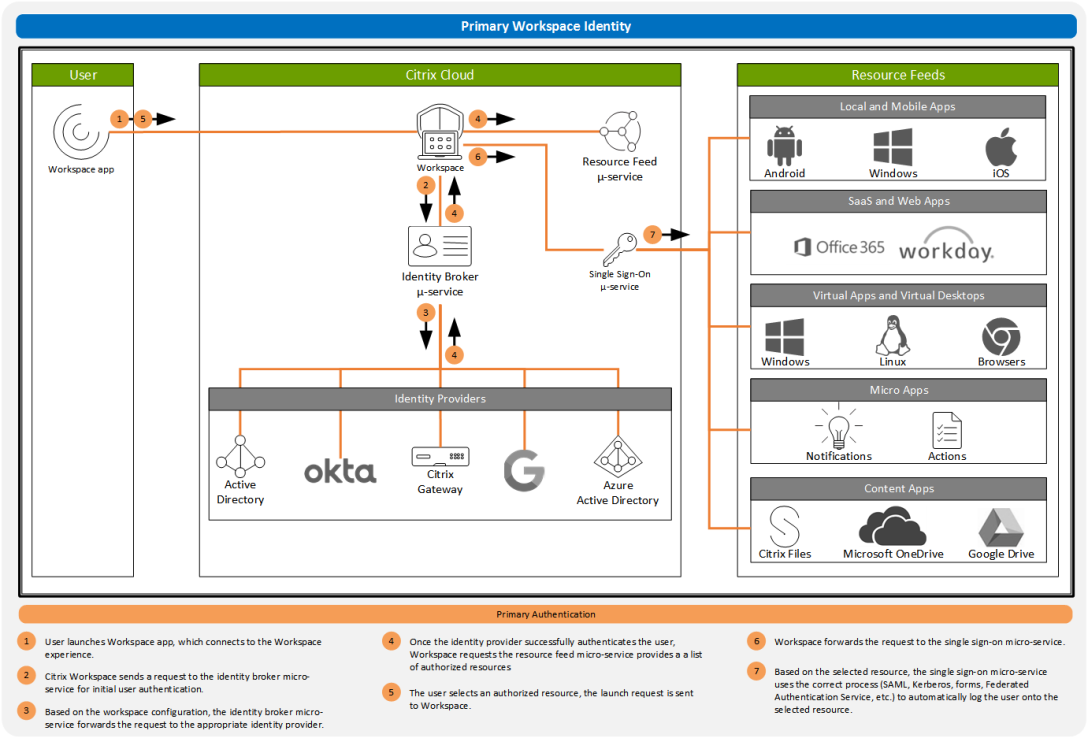
Citrix Workspace Authentication: Overview
One of the major issues with the current state of the end user computing environment is the number of identities a user is required to remember. Almost every service or application a user subscribes to requires the user create a new identity and password. With so many identities, almost all of us use the same… Continue reading Citrix Workspace Authentication: Overview
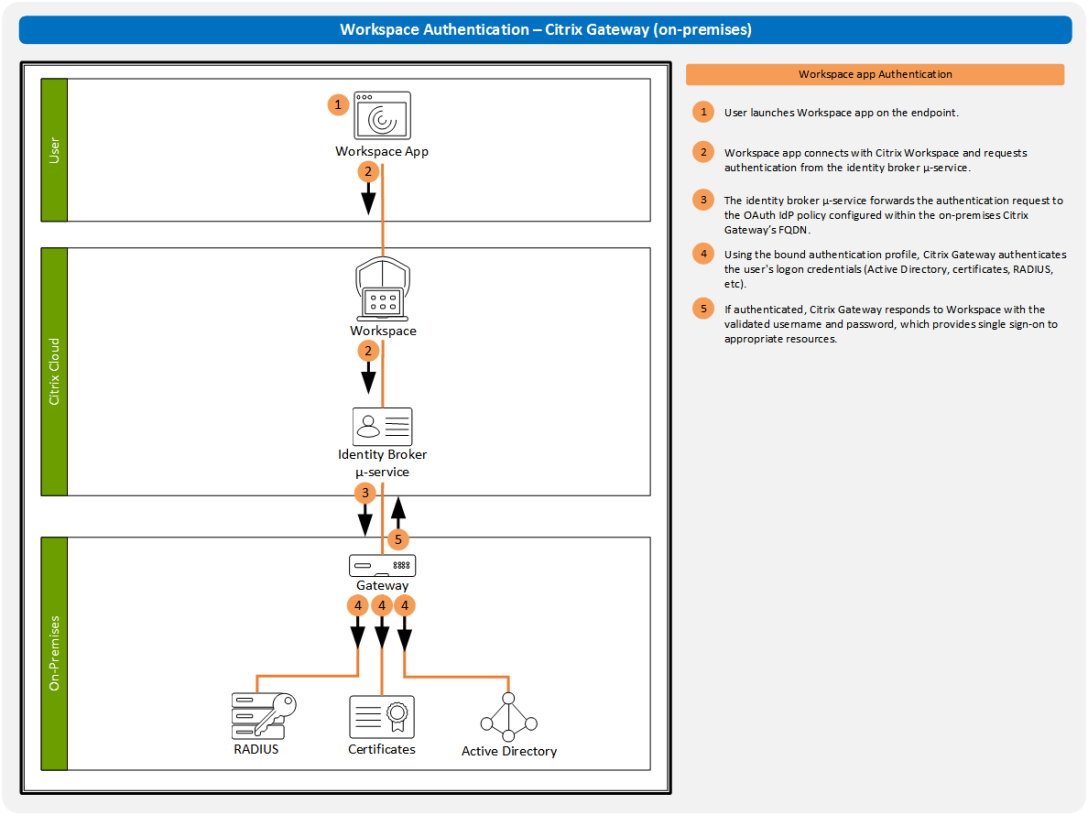
Citrix Workspace Authentication: Citrix Gateway
One of the challenges with using cloud services is getting the same experience you had in an on-premises deployment. For the past 20+ years, many Citrix Virtual Apps and Desktop deployments utilized a Citrix Gateway to provide an ICA proxy through the firewall. For external users, Gateway also authenticated those users. Over the years, admins… Continue reading Citrix Workspace Authentication: Citrix Gateway
Authentication: Two-Step Verification
So far, I’ve realized the following I have way too many identities Password complexity rules are implemented incorrectly Multi-factor authentication will provide additional authentication security So let’s look at one of the most basic forms of MFA. Unfortunately, I’ve seen this take on many names: Two-Step Verification Two-Step Authentication One-Time Password After providing your username… Continue reading Authentication: Two-Step Verification
Authentication: Passwords
<Sarcasm> Passwords. I love them. I love them so much, I have over 150 of them. </Sarcasm> We have our identity and we provide it to a system. In order to prove we are who we say we are, we need to authenticate. Passwords are one method for authentication. In theory, passwords are easy, but in… Continue reading Authentication: Passwords
Authentication: Your Identity
Most of us ignore authentication because it is seamless with us using our Active Directory username to log onto a domain-joined Windows 10 PC. But when we expand beyond Windows, there are so many other things to consider. I avoided learning about authentication for a long time. So many technologies. So many acronyms. So many… Continue reading Authentication: Your Identity